The Organisation of Year One A.C (After Covid19) Part 2/2
Credit to : Koh Ching Lan
Head of EUC, Net One Asia Pte Ltd
In this post, we continue on to Part II of The Organisation of Year One – A.C (After COVID19), as to how Net One Asia’s Workstyle Innovation (WSI) practice looks at 3 key services capabilities to give you the “Edge” in providing the Next Normal access services.


#1 – Rethink : Methods of Connection from Remote
Think Lightweight – Micro Tunnel Services
As more remote access becomes a cornerstone of working culture or the new normal, a traditional full-device VPNs access will have its limitation. VMware Micro Tunnel technology provides an alternative to compliment traditional full VPN access.
Innovating into establishing connectivity at an application level, instead of on a per-device basis. When an authorized app launches, VMware Tunnel establishes a silent connection for seamless and secure access.
Micro Tunnel Per-App VPN
Per-App VPN allows you to configure traffic rules based on specific applications. When the VPN is configured, it connects automatically when a specified app starts and sends the application traffic through the VPN connection, but not traffic from other applications. With this flexibility, your data remains secure while not limiting device access to the Internet at large.
By setting specific applications to start and use the VPN connection, only the traffic from those apps will use the VPN and not all other devices traffic. This logic allows you to keep corporate data secure while reducing the bandwidth sent through your VPN.


#2 – Rethink : Delivery and Interaction of Applications and Data
Think VPN-LESS – Digital Platform Services
The fast evolution landscape of critical business applications has created a challenge to IT in terms of managing applications under a unison interface and securing the access to these apps. On top of it, with the proliferation of various types of devices, implementing a one size fits all based on traditional EUC technology will not be advisable.
The word: “VPN-LESS” does not mean Full-VPN device access is inappropriate. It is to rethink the approach, to better deliver both apps and data due to the increasing adoption of SaaS, Web-based applications in a digital mobile work culture. Fundamentally, it is to rely less on VPN to grant access to corporate resources.
VMware Workspace ONE is VMware’s digital workspace solution. It is a digital platform that delivers and manages any app on any device by integrating access control, application management, and multi-platform endpoint management. Workspace ONE is built on the unified endpoint management (Workspace ONE UEM, formerly known as AirWatch) technology that integrates with virtual application delivery (VMware Horizon) on a common identity framework. The platform enables IT to deliver a digital workspace that includes the devices and apps of the business’s choice, without sacrificing the security and control that IT professionals need.
Consumer Simple Enterprise Secure
Unified Apps Catalog – A single interface where your users will “see” all the various applications type even legacy applications. VMware Workspace One UEM classifies applications as internal, public, purchased, and Web and you upload applications depending on the type end-users can get password-less single sign-on to a catalog that provides them access to virtually any app. This includes mobile apps, web apps, cloud apps, and Windows apps.
Provide easy access to all the apps your end users need to do their job either through a catalog available through a browser or the Workspace ONE native mobile app
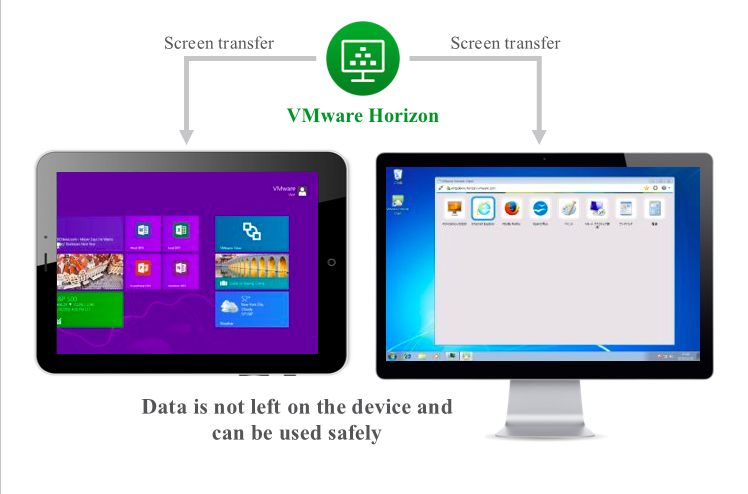
Horizon Services – VMware Workspace One Horizon services provides an alternative to remote terminal session. It not only provides an enterprise-class application publishing solution but also virtual desktop as well. And with its native Blast extreme display protocol, which is designed to be intuitive in terms of performance over corporate network. This helps IT to enhance its applications delivery services level which includes thick client applications.
From IT administrator stand-point, VMware Horizon Service with its Image Management and App Volumes features helps to ease the management of fully patched operating system image, and the basic application load, and the respective patches, version control of your images. And having different user groups who need access to different applications.
Content Secure Share – VMware Workspace One Content Gateway provides a secure and effective medium for end users to access internal repositories like Sharepoint, Fileshare.
It provides levels of access to your corporate content. Your end users can remotely access their documentation, financial documents, board books, and more directly from content repositories or internal fileshares. As files are added or updated within your existing content repository, the changes immediately display in VMware Workspace ONE Content. Users are granted access to their approved files and folders based on the existing access control lists defined in your internal repository.


#3 – Rethink : Secure Trust of Remote Access
Think Adaptive Based – Secure Access Control Services
The shift from a common set of security policy to a more adaptive based approach stems out of necessity. The reality is the changes in workstyles with regards to how end users expect to interact with productivity tools, devices, and the apps that is increasing outside of corporate network wall requires a rethink to enable secure access to corporate resources.
Universal Strong Authentication
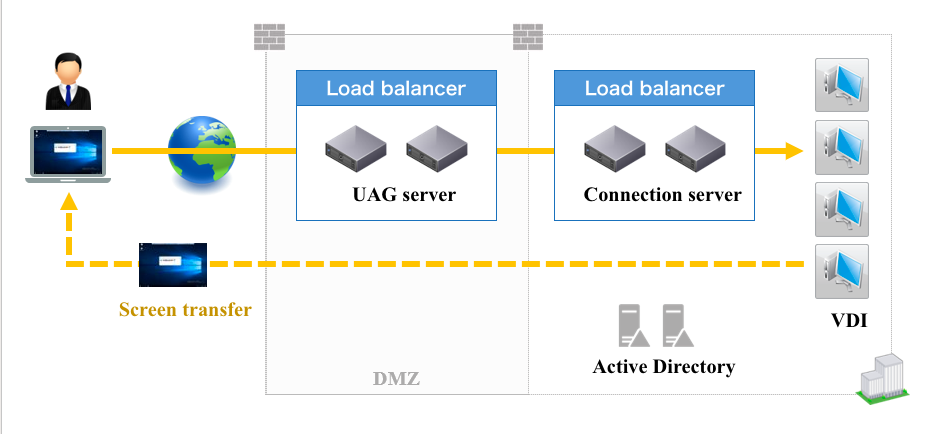
Who are you and can I trust you? – The key step to secure the access of your corporate resources is to establish the identity of your user request and ensure they have the right authorization to access the requested resources. VMware Workspace One UAG can be configured to perform the initial user authentication itself. Its capability to support identity management provider user store, which does not necessarily have to be Active Directory.
It has the capabilities of reverse proxy and support legacy web applications that still is using Kerberos authentication methods and bridge the identity protocol by converting SAML and or certificate based to Kerberos authentication. Hence utilising a more modern authentication method over an external connection to grant access to web application that is still using Kerberos authentication method.
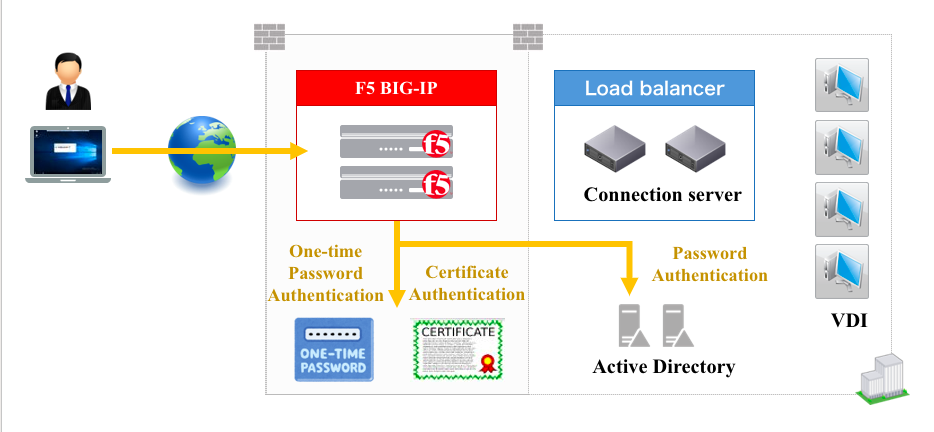
User Name & Password isn’t enough – To gain a higher trust posture, VMware Workspace One UAG supports multi-factor authentication with the supported user authentication method that include:
- Active Directory domain password
- Kiosk mode
- RSA SecurID two-factor
- RADIUS via a number of third party, two-factor security-vendor solutions
- Smart card, CAC, or PIV X.509 user certificates
- SAML
Its integration with 3rd party identity management provider to give a seamless SSO experience while enhancing the security access to all types of application.
Contextual Access
Dynamic & Granular Access Policy – It can be dynamic in determining the appropriate access policy for various connection request. VMware Workspace ONE with its Workspace One Access combines identity and device management to enforce access decisions based on a range of conditions from strength of Authentication, Network Range, Location, and Device Compliance.
It provides a powerful policy engine so that you can mix and match these inputs to make dynamic decisions on the level of access end-users get. This means that if you need to lock down access to sensitive data from remote users on unmanaged devices, you can do that in just a few clicks. But we go one step further. We provide the end-user workflow for endpoints to get into a state that results in compliance, and thereby access.
Granular conditional access policies can be applied on a per-application basis to enforce authentication strength and restrict access by network scope or through any device restriction.
Example:
For Windows 10 and other devices, VMware Workspace ONE can apply device profiles that allow you to configure security settings that will keep devices secure (encryption, Windows Updates, etc), but also some features that will really improve the experience for end users (configuring Wi-Fi and VPN for example)
Data Protection – Advanced data leakage protects against rooted or jailbroken devices, allow list, and deny list apps, open-in app restrictions, cut/copy/paste restrictions, geofencing, network configuration, and a range of advanced restrictions and policies.
For Office 365, the integration with the Office 365 Graph API can manage the DLP settings across the suite of Office applications to ensure security.
Preparing to be the organisation of year one A.C. begins right at the digital workspace domain. Let’s rethink the way Remote Connection is done, how Applications and Data is delivered, and enable an adaptive secure control of this access. Start to unify with VMware Workspace One UAG Technology to be the Edge Multi-Services Hub to provide a platform for your End User Computing services in this new normal.
Contact Us for a scheduled Virtual Meeting to discuss your requirement!
Net One Asia Workspace as a Service is a intelligence driven digital workspace managed service platform that simply and securely delivers and manages any application and desktop on any device by integrating access control, application management, and multi-platform endpoint management.